Mobile system Encryption Mobile units, like smartphones and tablets, retail outlet an unlimited amount of money of personal and delicate information and facts. cell system encryption requires scrambling the data on the product making sure that only you, together with your unique password or PIN, can obtain it.
selections produced without the need of questioning the outcome of a flawed algorithm may have critical repercussions for human beings.
Encrypted data is uploaded to Azure, and only authorized shopper-facet apps can decrypt and access the data utilizing the securely managed keys.
With this encryption, data can only be accessed with the proper encryption essential. FDE delivers a significant standard of safety for data at rest, as it safeguards against unauthorized obtain whether or not the storage product is stolen or lost.
workers which have entry to business-vital details need to know the significance of securing data at relaxation to circumvent data loss. Verizon's 2022 DBIR uncovered 82% of breaches about the preceding yr associated a human aspect. frequent teaching may help mitigate the chance of human error.
Data is central to most every single component of modern small business -- staff and leaders alike need reliable data for making every day conclusions and program strategically. This tutorial to explores threats to data and clarifies the best methods to keep it protected in the course of its lifecycle.
When you hook up with click here a VPN, all your community website traffic is encrypted and tunneled from the VPN's secure server. This prevents anybody from snooping on or interfering with all your data in transit.
less than regulations like GDPR, data breaches involving encrypted data the place the keys are usually not compromised may not require reporting. CSE makes sure that the data is encrypted in a method that fulfills these regulatory specifications.
corporations that encrypt their sensitive data often conclude that their data is totally guarded, but that isn't the situation. classic encryption won't go over among the big vulnerabilities that providers face currently: an attacker obtaining unauthorized, direct use of the database.
Furthermore, you need to be practical with critical dimensions as huge keys could cause concerns. for instance, if you employ AES symmetric encryption, you don't need to utilize the best AES 256 cryptography for all data.
Smart classification equals intelligent security: By categorizing all of their data and being familiar with its threat profile in just about every condition, corporations is going to be in the most beneficial posture to pick the best defense actions.
electronic mail encryption is not really optional: Encrypting electronic mail guarantees its contents are safe and that any attachments are encoded so they can’t be read by prying eyes. Encryption is usually applied to email delivery, directory sync and journaling, supporting with both stability and classification.
whether or not your system is lost or stolen, the data stays shielded so long as your password is not compromised.
Encryption is employed by forty two% of respondents for shopper data, rating it since the fifth most often encrypted type of information in firms. Implementing data at storage encryption can help in regulation and most significantly the have confidence in of customers.
 Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now! Jennifer Grey Then & Now!
Jennifer Grey Then & Now!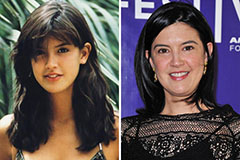 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Mary Beth McDonough Then & Now!
Mary Beth McDonough Then & Now! Katey Sagal Then & Now!
Katey Sagal Then & Now!